??Furthermore, Zhou shared which the hackers started off making use of BTC and ETH mixers. Because the identify implies, mixers combine transactions which additional inhibits blockchain analysts??power to monitor the funds. Pursuing the use of mixers, these North Korean operatives are leveraging peer to see (P2P) distributors, platforms facilitating the immediate obtain and selling of copyright from just one user to a different.
This tactic seeks to overwhelm compliance analysts, regulation enforcement, and blockchain analysts by undertaking Countless transactions, both equally by DEXs and wallet-to-wallet transfers. Following the expensive attempts to hide the transaction path, the last word aim of this process will be to transform the cash into fiat currency, or forex issued by a govt much like the US dollar or maybe the euro.
Typically, when these startups try to ??make it,??cybersecurity measures may possibly become an afterthought, particularly when businesses absence the cash or staff for this kind of actions. The situation isn?�t unique to Individuals new to small business; however, even effectively-proven providers may let cybersecurity fall for the wayside or may lack the training to comprehend the speedily evolving menace landscape.
Get personalized blockchain and copyright Web3 information sent to your app. Earn copyright benefits by Mastering and completing quizzes on how particular cryptocurrencies work. Unlock the way forward for finance Along with the copyright Web3 Wallet, your all-in-one particular copyright wallet inside the copyright app.
Be aware: In exceptional circumstances, dependant upon mobile provider settings, you may have to exit the web site and check out yet again in a handful of hours.
three. To incorporate an extra layer of safety for your account, you may be asked to enable SMS Authentication by inputting your phone number and clicking Mail Code. Your technique of two-component authentication might be transformed at a later day, but SMS is needed to complete the register course of action.
Also, harmonizing polices and reaction frameworks would make improvements to coordination and collaboration endeavours. Harmonization would allow for for relieve of collaboration throughout jurisdictions, pivotal for intervening from the smaller Home windows of chance to regain stolen money.
Some cryptocurrencies share a blockchain, even though other cryptocurrencies run by themselves individual blockchains.
All transactions are recorded on the internet in the electronic database referred to as a blockchain that employs highly effective just one-way encryption to be certain stability and evidence of ownership.
2. copyright.US will send out you a verification electronic mail. Open up the email you utilized to enroll in copyright.US and enter the authentication code when prompted.
copyright exchanges fluctuate broadly during the companies they supply. Some platforms only provide the opportunity to buy and market, while some, like copyright.US, offer Innovative services Along with the fundamentals, together with:
Further safety actions from either Protected Wallet or copyright might have diminished the chance of the incident developing. For instance, implementing pre-signing simulations would've authorized staff members to preview the place of the transaction. Enacting delays for big withdrawals also would have offered copyright time to review the transaction and freeze the resources.
All round, developing a secure copyright sector would require clearer regulatory environments that organizations can properly operate in, modern plan options, increased safety criteria, and formalizing Intercontinental and domestic partnerships.
Before sending or obtaining copyright for The 1st time, we advise reviewing our advisable most effective procedures On the subject read more of copyright security.
Enter Code whilst signup to acquire $one hundred. I have been working with copyright for two decades now. I actually appreciate the modifications in the UI it acquired about enough time. Rely on me, new UI is way much better than Many others. Nevertheless, not every thing On this universe is perfect.
Security begins with knowledge how builders obtain and share your data. Information privacy and security methods could fluctuate determined by your use, area, and age. The developer furnished this information and facts and could update it over time.}
 Angus T. Jones Then & Now!
Angus T. Jones Then & Now! Tahj Mowry Then & Now!
Tahj Mowry Then & Now! Jenna Jameson Then & Now!
Jenna Jameson Then & Now!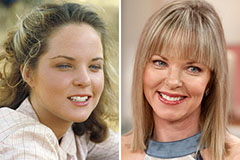 Melissa Sue Anderson Then & Now!
Melissa Sue Anderson Then & Now! Dawn Wells Then & Now!
Dawn Wells Then & Now!